Playing around with Packet Captures
A quick overview of some packet capture events
Trevor Krzesnik
11/26/20245 min read
As I made my way through the different areas of wireless, one of the most intimidating things for me was getting into packet captures. The idea of navigating through hundreds to thousands of packets just sounded overwhelming. After spending a little time in the CWAP book and playing around in Wireshark it wasn't as scary as I thought it would be. Everything is labeled for you in the packet capture and using filters will drastically improve your time in narrowing down what you're looking for. Another thing that can help you navigate through your packet captures is to apply coloring rules. The color rules I used in my captures below are from MetaGeek. Below are a few packet captures I did as I was learning how to navigate through them.
WPA2-PSK Failed
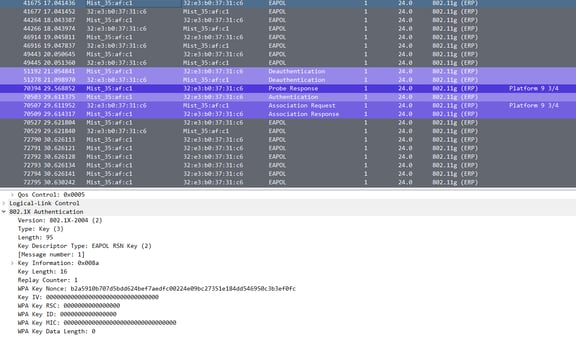
Message 1
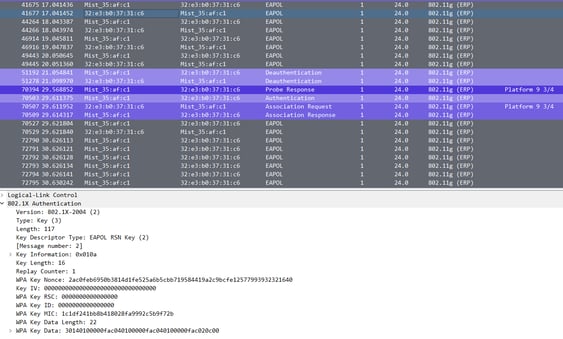
Message 2
As you can see at the top of the packet capture, the EAPOL messages 1 and 2 of 4 repeat between the supplicant (laptop) and the authenticator (access point). When you see the messages repeating like this, this would be your indicator for authentication failure. After a few failed attempts, my device is then unauthenticated and then starts through the authentication and association response again.
802.1X Full Authentication
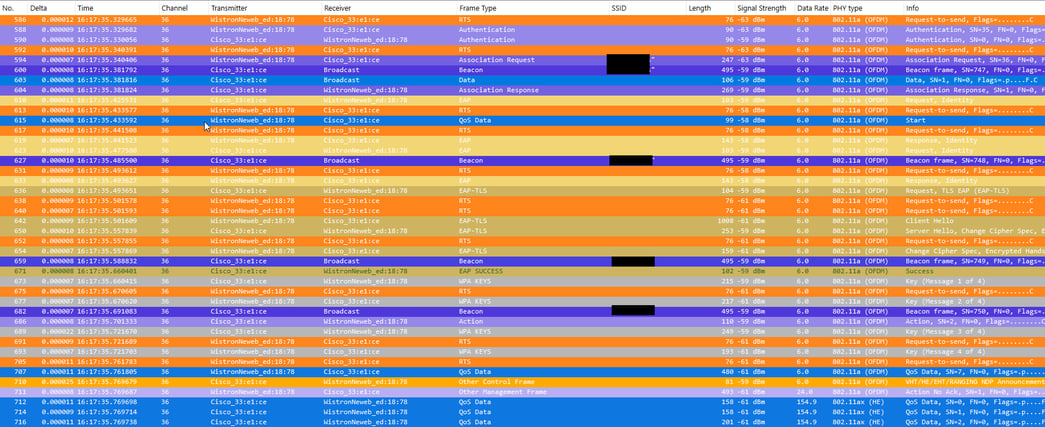
Above is a capture that shows the connection process for an 802.1X network from start to finish. You can see the authentication messages between the device and the access point followed by an association request and response. The next step in the connection is to pass extensible authentication protocol (EAP) messages between the supplicant (device), authenticator (access point), and the authentication server (RADIUS). An 802.1X network is port-based access control and will have a controlled and uncontrolled port. A quick summary of the two:
Uncontrolled Port
Used for authentication
blocked from passing general data traffic between two STAs until an IEEE 802.1X auth procedure
not even DHCP addressing occurs until AFTER authentication
allow data communications across the controlled port
used for exchanging auth frames
Controlled Port
blocks all other traffic until the supplicant has completed 4-way handshake
Passes protected data
authentication completes successfully, data protection is enabled to prevent unauthorized access
when the client gets a DHCP address and starts functioning as a network-connected device
allows communication of data frames
The first messages are between the device and the access point asking for the device to identify itself. Once the device is identified, the access point will forward it along to the authentication server. As you can see in this instance, we are using EAP-TLS so this will be certificated based authentication. After we successfully complete EAPoL, we still do not have the controller port open so we need to complete the four-way handshake to complete our authentication.
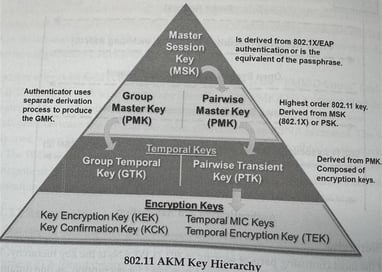
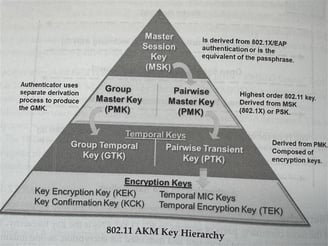
CWSP Book pg. 204
Here is a picture of the 802.11 AKM hierarchy and a brief description of how the AKM keys are derived as part of the four-way handshake as well as a minimized view of our handshake in the connection process. Here is where we will derive our keys to encrypt and decrypt messages. It all begins with the Pairwise Master Key which is the PSK in a WPA/WPA2-PSK network or a Master Session Key which is derived from the 802.1X authentication. Once this process is complete, the controlled port is now open and we can send data across the network.

Retry Packet
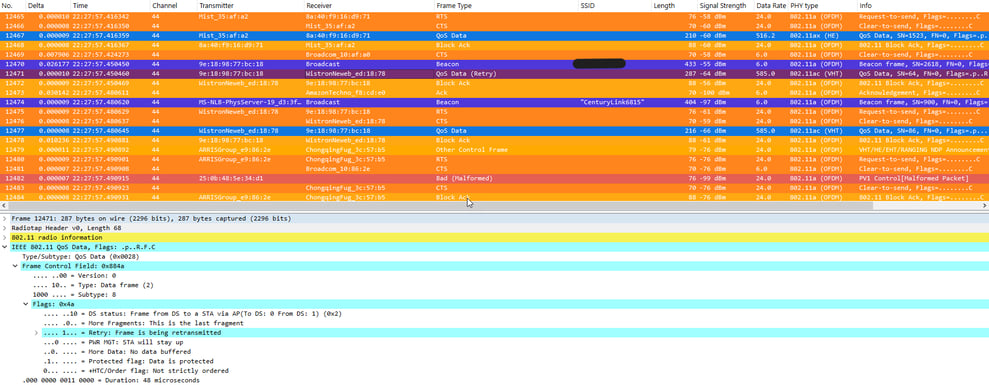

Here would be an example of a packet retry and it is highlighted red in our picture. As part of the coloring rules, where to navigate in order to find your bit that notifies of a retry is highlighted in blue as well. Our network will begin to slow down if we have too many of these filling our air time.
Beacon Frame
One of the most important frames you will see in your packet captures will be your beacon frames. Your beacons are going to tell you and your devices everything you need to know about the network you are connecting to. To highlight a few you see here, you can see what our mandatory data rates are set to along with the supported data rates. The next one you see is the current channel the access point is using followed by our TIM which will indicate whether there are buffered frames for a device that was in power save mode. Following that is going to be our country code which is set to US.
Jumping down a few, and you can see it highlighted, will be our RSN information element. This will let our devices know whether or not our network meets the requirements for a Robust Secure Network or 802.11i. Allowing WPA, WEP, or Open, does not meet requirements for RSN so you would not see this tag in your beacons. Opening this tag will tell you what your pairwise cypher suite as well as your auth key management information.
The last ones I will cover will be how you know what type of devices (802.11n, ac, ax) your access point will support. Most APs at this point are going to be at least 802.11n so you will see the HT capabilities and information elements if that's the case. If you see the VHT (very high throughput) capabilities and operations tags, your AP will support 802.11ac devices. You can find your supported MCS rates under your capabilities tab. Our last potential device support tag will be an extended tag that has your HE (high efficiency) capabilities and operations tags. If you see HE tags then your access point will support 802.11ax devices.
Getting into the weeds of packet captures can be intimidating and overwhelming. There's lots of information to digest but it's all there to help you understand how efficient your network is performing as well as validating your SSIDs and what you are broadcasting.
Sources - Certified Wireless Security Professional CWAP 404 - 2nd Edition
